AWS Key Management Service
What Is AWS KMS?
AWS Key Management Service (KMS) is a fully managed service to create, store, and control encryption keys in order to encrypt your data.
Some important points:
- KMS is a highly durable and available service.
- KMS encryption keys are regional.
- The service leverages Hardware Security Modules (HSM) under the hood, which in return guarantees the security and integrity of the generated keys.
- It offers easy key rotation and logs all events related to a key to AWS CloudTrail.
Key Concepts
Customer Master Keys (CMKs)
Customer master keys never leave the AWS KMS service unencrypted. They contain metadata like key id, creation date, etc. They can be used to encrypt/decrypt arbitrary chunks of data that are no greater than 4 KB.
Typically, you use CMKs to generate, encrypt, and decrypt the data keys that you use outside of AWS KMS to encrypt your data. This is known as envelope encryption.
CMKs can be:
- Customer-managed — These are created and managed by the AWS user. Access to it can be controlled using the AWS IAM service.
- AWS-managed — These are created and managed by AWS on your behalf. They can be identified by the format aws/service-name.
- AWS-owned — These are not in your AWS account. They are part of a collection of CMKs that AWS owns and manages for use in multiple AWS accounts. They cannot be viewed or managed by the user.
Data Keys
These are symmetric keys generated by AWS KMS, which can encrypt/decrypt large amounts of data. AWS KMS does not store, manage, or track data keys, or perform cryptographic operations with data keys. You must use and manage data keys outside of AWS KMS.
Basic Encryption Using AWS KMS
It is a straightforward way of encrypting/decrypting your data using AWS CMKs.
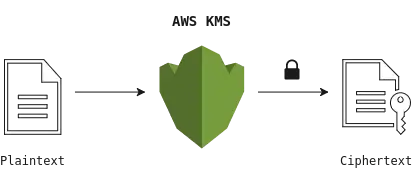
Limitations:
- CMKs can encrypt/decrypt only up to 4 KB of data at a time.
- It can be costly to send huge amounts of data to an Amazon service every time you need to encrypt/decrypt it. Also, it can involve security issues like man-in-the-middle attacks, etc.
Envelope Encryption
This makes use of both data keys and CMKs. It uses data keys to encrypt plain text and CMKs to encrypt data keys.
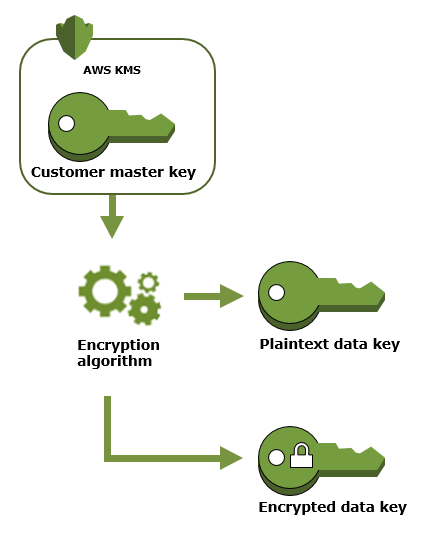
- Generate a data key using AWS’s GenerateDataKey operation. AWS KMS uses CMKs to generate data keys. It will return a plaintext copy of the data key and a data key encrypted using CMK.
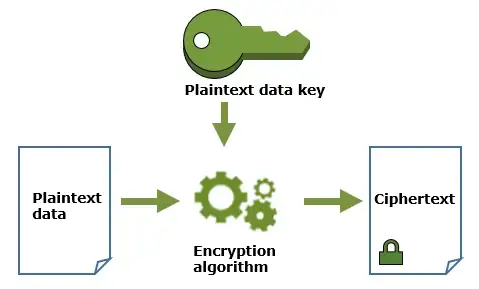
2. Encrypt data with a plaintext data key. AWS KMS cannot encrypt data using data keys, but you can use data keys outside AWS KMS to encrypt/decrypt your data. After encrypting plaintext data using a plaintext copy of a data key, remove the data key from memory as soon as possible for security. The encrypted copy of the data key is stored for decryption.
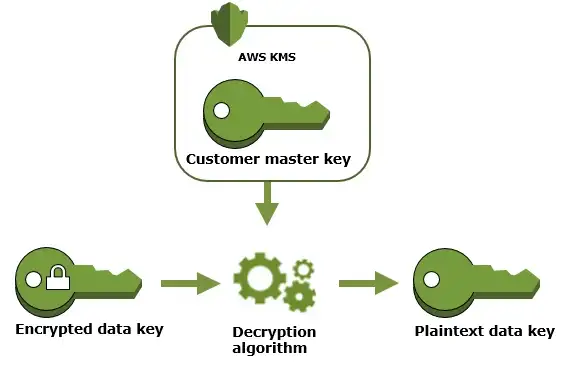
3. Decrypt data using an encrypted data key. To decrypt the data, use AWS KMS’s decrypt operation to decrypt an encrypted data key to get the plaintext copy of the data key (decrypted using CMK). Then use this plaintext data key to decrypt ciphertext outside AWS KMS.
Here are the advantages of using envelope encryption:
- You don’t need to protect the data keys. You can simply store encrypted data keys along with encrypted data.
- It enables you to combine the strengths of both symmetric key encryption algorithms and public-key encryption algorithms.
- You get a performance boost, as you don’t need to send large amounts of data to Amazon servers.
- Instead of re-encrypting your raw data with multiple data keys, you can re-encrypt your data keys.
Some Good Resources
https://docs.aws.amazon.com/kms/latest/developerguide/concepts.html
METAVIEW
An irregular digest about experiments with 2-3 interwebz bookmarks.
- subscribers